🔐 Proxy Design Pattern: Database Access Control
📘 Scenario:
Imagine you are building a user management system with access to critical database operations like Insert, Update,
Delete, and Select. However, you want to restrict access so that only authorized users can perform these actions.
For example, only an admin with the correct username (Tharindu) and password (deltaCodex8754)
should be able to modify the data.
Without proper control, unauthorized users could execute sensitive commands. That’s where the Proxy pattern helps!
⚠️ Problem:
- Direct access to the database class can be dangerous or insecure.
- No authentication logic separates user access and core database logic.
- This could result in untraceable or malicious queries by unauthorized users.
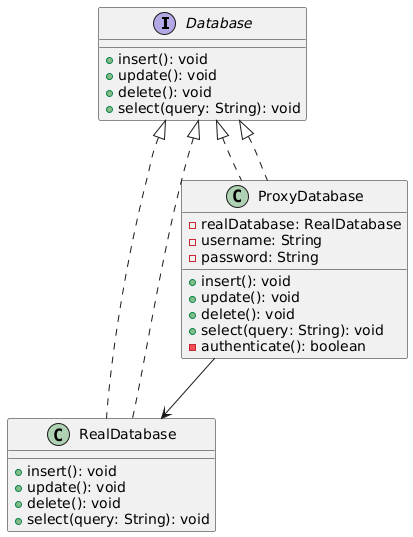
💡 Proxy Pattern Solution:
We create a ProxyDatabase class that wraps around the real RealDatabase and acts as a gatekeeper.
It performs authentication before delegating database operations. This keeps the core database logic clean and adds
an extra layer of security.
🖥️ Output:
[System] ✅ Login successful.
[ProxyDatabase] ✅ Authenticated. Delegating insert().
[RealDatabase] Inserting data into the database.
[ProxyDatabase] ✅ Authenticated. Delegating update().
[RealDatabase] Updating data in the database.
[ProxyDatabase] ✅ Authenticated. Delegating delete().
[RealDatabase] Deleting data from the database.
[ProxyDatabase] ✅ Authenticated. Delegating select().
[RealDatabase] Selecting data with query: SELECT * FROM users;